Fuelling RootSecure’s Strategic Growth
While we knew about RootSecure for a while – including personally knowing about half their team – we didn’t really know exactly what they did (or how) prior to actually diving deeply into this project.
Elsewhere on this site, we’ve summarized the RootSecure success story; this post provides an extended explanation of the project execution.
Background
Our first meeting with RootSecure was a fairly general discovery session: we asked about their current activities, their goals for the year, and where they saw marketing fitting into their overall strategy. (Because we all knew each other from earlier in our careers, we didn’t need to get into credentials, references, and that sort of thing.)
From that short conversation, we learned that RootSecure had an active digital pay-per-click (PPC) marketing campaign, they wanted to refresh their website and solution brochure, and they had some exciting products on the horizon. RootSecure were also starting to encounter a problem common to start-ups: as the products evolve and as more content get created, the message starts to get a bit fuzzy – so they wanted to tighten things up in that regard.
We ultimately decided that the most effective way to start would be to produce a Messaging Guide that would serve as a single source of truth.
We proposed a few different approaches that might work; we ultimately decided that the most effective way to start would be to produce a Messaging Guide that would serve as a single source of truth. That document would serve as a guide for Cromulent to produce a new solution brochure and an overview presentation. The Messaging Guide would also serve as the basis for the website refresh (to be done by RootSecure’s in-house marketing team) and to inform tweaks to the ongoing digital campaign.
Phase I: Message and Content Refresh
We began by learning everything we could about RootSecure (mission, plans, products, underlying technology, etc.), their customers, their competitors, the industry as a whole, and so on:
- To understand RootSecure’s product and technology, we spoke directly with the engineers who built particular features and products
- To understand the appeal of RootSecure’s solutions, we spoke with customers and partners to ask why they’d chosen RootSecure, what they’d say to friends in the industry when asked about the solution, etc.
- To understand RootSecure’s competitors, we conducted fairly extensive research
- To understand industry dynamics and to ensure unbiased assessments, we spoke with a renowned security consultant
Informed by this initial research, we also dived deeply into different security philosophies, frameworks, technologies, and so on; conveniently enough, earlier in his career Lee was a product manager for a network security product, so he was reasonably well-versed in this sort of thing.
It’s worthwhile to note, also, that RootSecure already had a number of reference customers who’d agreed to be profiled in videos; these videos were a valuable source of authentic customer language and insight into what customers valued in the solution.
These videos were a valuable source of authentic customer language and insight into what customers valued in the solution.
From this research, we were able to answer important questions, including:
- What problems are RootSecure’s potential customers trying to solve?
- How do RootSecure’s capabilities address those problems?
- What makes RootSecure’s capabilities unique in the marketplace?
- What do customers truly value about RootSecure’s solutions?
Using the answers to these questions, and more, we prepared a comprehensive ~20-page Messaging Guide that included messaging for:
- RootSecure, the company, including a new boilerplate, the company origin story, and answers to the important question, “Why RootSecure?”
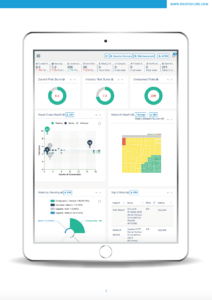
- The RootSecure Dashboard: a cloud-based security operations center that provides visibility into continuous cyber risk assessment
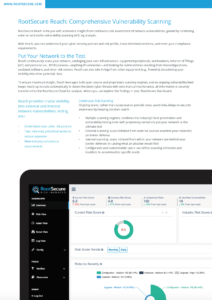
- RootSecure Reach, which provides actionable insight from continuous risk assessment of network vulnerabilities
Importantly, the Messaging Guide included detailed problem-oriented feature descriptions, additional context on the industry and competitive technologies, information about RootSecure’s target customers, and message maps that explained how to tailor delivery to different audiences and personas.
Knowing that other features and products were forthcoming later in the year, we made sure to develop messaging that could easily accommodate additions to the cyber security portfolio.
We then used the Messaging Guide as the base to produce a four-page brochure and an overview presentation. In the presentation, we went a little bit deeper into the overall context (e.g., comparing RootSecure’s continuous vulnerability scanning approach against alternatives) than we did in the brochure; both pieces included customer testimonials, which often go a long way to reducing perceived risk of adopting a new solution.
Feedback from RootSecure’s customers, partners, and team was very positive – we were even told that a new sales leader was using the Messaging Guide as a valuable onboarding resource to get new business development representatives ramped up and on message immediately!
Phase II: Product Extension
The items delivered in Phase I addressed RootSecure’s immediate content needs, but we knew all along that updates would be needed to support the launch of two powerful new products:
- Scout, which extends visibility inside devices, with continuous host-based monitoring
- Echo, a turnkey social engineering simulator
When the time came (a couple of months later), incorporating the addition of Scout and Echo into the messaging was relatively straightforward:
- The company messaging was extended to account for the new solution breadth
- Scout and Echo each got their own sections within the Messaging Guide
- We introduced a portfolio/architecture diagram to visually represent how all the pieces fit together, making it easier for people to tell and to understand full RootSecure solution
With the addition of Scout and Echo, we refreshed the brochure and extended it into an 8-pager; accordingly, we also added a few new slides into the overview presentation.
Given the technical nature of their product, and the larger context of many vendors making similar claims, we needed to include enough descriptive information to explain the meaningful differentiation of RootSecure’s solution breadth and feature specifics.
A few things were particularly important to us when we prepared the brochure:
- We wanted to make sure to show off some of the product’s visuals, so we devoted significant space to large, clear renderings of the RootSecure Dashboard
- Given the technical nature of their product, and the larger context of many vendors making similar claims, we needed to include enough descriptive information to explain the meaningful differentiation of RootSecure’s solution breadth and feature specifics; we wanted to leave no doubt in any prospect’s mind after reading this brochure that RootSecure’s solution powerfully addresses the cyber risk problems the prospect is trying to solve
- The back page is devoted to reducing perceived risk: we included three customer references, distilled from the YouTube videos; additionally, RootSecure’s origin story serves as its own point of validation – the product was originally developed as part of a managed IS/IT services offering, but enormous customer demand led to it being spun off as its own company
Phase III: Spreading the Word
RootSecure’s customers love the company’s solutions, and RootSecure plans to continue their expansion, but to do so they need to grow their team. Competing for talent in the Waterloo Region isn’t especially easy, as a small number of more well-known companies tend to garner most of the headlines.
To help attract the talent that will in part fuel their growth RootSecure wanted to increase their local profile. We helped by introducing RootSecure to some local media contacts; thankfully, those introductions resulted in coverage in both the print and online editions of The Waterloo Region Record and an online article with Communitech (a local public-private innovation hub).
Success Factors
So, what factors led to the project’s success?
First and foremost, expectations were clear from the beginning and mutually understood. Both parties knew why we were working together and what we aimed to achieve.
We had a literal seat in the office, which let us just saunter over to an engineer to get deep and specific questions answered in detail.
Second, RootSecure opened their doors to us: they introduced us to some of their customers, let us sit in on sales pitches, and were generous with their time. We had a literal seat in the office, which let us just saunter over to an engineer to get deep and specific questions answered in detail. This level of access kept things moving very quickly.
Third, RootSecure have a really great solution. It’ll sound cheesy, but we really had a lot to work with: powerful technology that addresses valuable real-world problems in meaningfully unique ways, and that’s already been validated with market adoption and adoring customers…? It practically writes itself.
There were some other factors (for instance, RootSecure already had presentation and document templates), but those are the big ones.
In Closing…
Working with RootSecure was very fun and rewarding: we couldn’t be happier to help them accelerate their growth by providing marketing insights, messaging, and content, and we genuinely enjoyed learning about their solutions.
It might sound odd, but while we knew about RootSecure for a while – including personally knowing about half their team – we didn’t really know exactly what they did (or how) prior to actually diving deeply into this project.
It’s always fun to learn new things and to work with great people =)
—
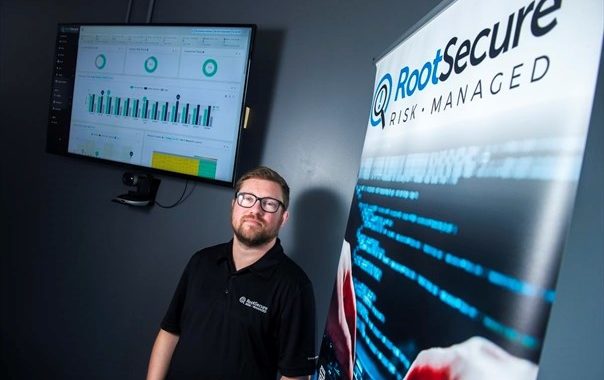
Feature Image: Ian Hassard of RootSecure poses with the dashboard of the company’s cloud system at RootSecure offices in Kitchener. – Andrej Ivanov , Waterloo Region Record